Toll Free: (844) 520-3539
Flexnet Networks LLC Blog
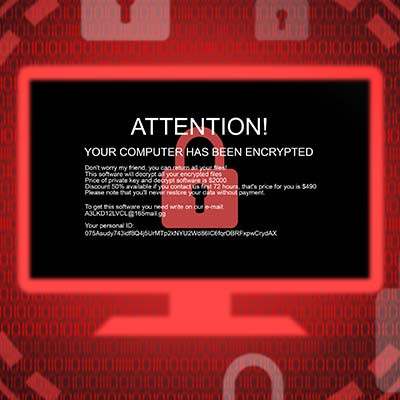
We’re hoping that you are actually reading this post to prepare yourself if your business were to face a ransomware attack, but if you are suffering from one right now, we encourage you to reach out to us immediately, whether you are a client or not. Ransomware spreads quickly, and once it has infected a system, there really isn’t much you can do to stop it. However, there are steps you need to take to come back from this gracefully.
With ransomware becoming one of the single most dangerous threats out there for small businesses, it’s more important than ever to know how to protect your company from its influence. Thankfully, there are measures you can take, including some very powerful ones like zero-trust policies that can thwart attempted ransomware attacks.
You don’t need us to tell you that ransomware is a problem (or maybe you do–we mean, it’s a huge problem). It’s dangerous to both businesses and individuals, and it has become such a common threat that all organizations need to have a plan in place to address it with their staff. Today, we want to highlight a three-part strategy that you can use to approach ransomware in the most secure way possible.
Okay, let’s say you’ve been infected by a ransomware attack, and (against our advice) you’ve elected to pay the ransom. That’s the biggest cost that comes with it, right?
Unfortunately, wrong. A ransomware attack comes with a lot more financial impact than just the payment the attacker demands. Let’s go over some of these other costs that can actually outpace that of the ransom.
Let’s begin by making one thing abundantly clear—all businesses and industries could potentially be targeted by ransomware, regardless of their size or target audience. However, as of late, some industries have been targeted more and more. Let’s examine some of the commonly targeted industries that ransomware is frequently waged against.
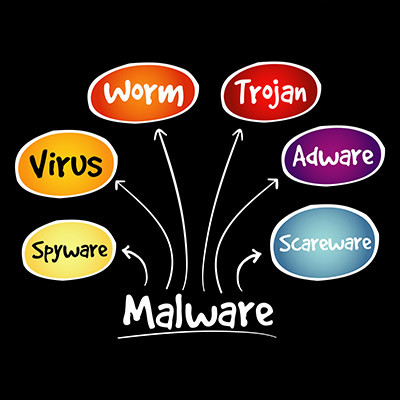
Network security could mean any number of things, but more often than not, people are using the term as a blanket statement against the dreaded idea of malware and its many forms. Today, we are discussing how vast the world of malware can be and how often you might find yourself misunderstanding what it exactly is. Knowing all this can help you identify if you have become a malware victim or not.
Ransomware is widely regarded as one of the worst modern cyberthreats out there today, and there's plenty of evidence to support this. These attacks and their aftereffects can devastate businesses of all industries. Let's consider why it is that ransomware is so dangerous, and what can be done to fight it.
There’s no way around it; ransomware is bad stuff, plain and simple. The first half of 2021 saw a massive increase in ransomware attacks that made the lives of countless individuals and business professionals difficult. However, a new trend is surfacing, and it’s one that you might be surprised to see: fake ransomware threats.
While it only makes sense to assume that a cybercriminal would focus specifically on those targets that would bring them the greatest profit—in other words, larger businesses—the reality of modern cybercrime renders this assumption grossly outdated. Let’s examine how different developments in ransomware have made it possible for cybercriminals to be far less discerning in who they target.
Ransomware is such a massive threat that all businesses should be aware of the latest news and findings regarding how it spreads and how it can be prevented. According to a recent report, the latest modes of transporting ransomware have been revealed. What can your organization do to keep ransomware off of its network? Let’s find out.
Ransomware has rapidly progressed from an irritating annoyance to a legitimate global threat, with the U.S. Justice Department officially going on the record and establishing that future ransomware investigations will be handled the same way that terrorism cases are now. Let’s review the reasons behind this policy change and how your business should respond.
Last weekend saw a significant cyberattack waged against the world’s largest meat processor and distributor, JBS S.A., that completely suspended the company’s operations in both North America and Australia… and as a result, has impacted the supply chains associated with the company. Let’s examine the situation to see what lessons we can take away from all this.
Headlines have been filled with news pertaining to the recent hack of Colonial Pipeline, which has created significant gasoline shortages up the east coast of the nation. While the pipeline has been restored, the way this was accomplished sets a dangerous precedent. On top of this, the attack seems to have set off bigger infrastructural changes in the political space.
If fortune smiles on your company, you won’t ever have to deal with what we are about to discuss: ransomware. For the past several years ransomware has been a major issue for businesses, governments, and individuals. Today, we will talk about ransomware, how there are different strategies, and how some people want to put a ban on ransomware payments.
When it comes to ransomware, we have always stood firm in our recommendation not to pay whoever is responsible for locking down your systems. However, due to the globalized nature of technology and cybercrime, it is even more important that companies don’t attempt to placate their attackers with the demanded funds. Otherwise, warns the United States Treasury Department, these victimized businesses could very well pay severe fines for doing so.